Application Security
Companies that identify and remediate software deficiencies early and often will generate software maintenance savings that reduce overall development costs and risk to operations. Weaknesses in application architectures have rapidly become the targets of choice for attackers. In fact, application security vulnerabilities have become one of the top information security issues facing organizations today. To stay ahead of the risks associated with the application layer, you must manage and maintain the security of every application deployed.
Capstone Security’s Application Security solutions can help protect your most critical enterprise applications from both internal and external threats. Our consultants can dramatically improve your organization’s ability to assess the security of existing applications as well as design, develop, test and maintain the security of applications in all phases of their development lifecycle.
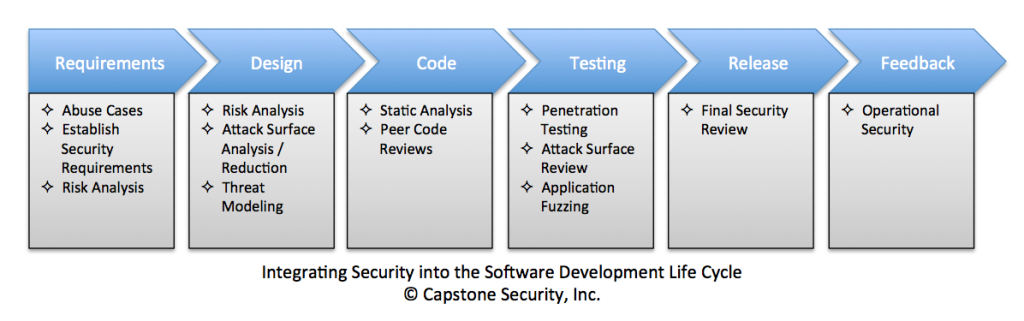
Integrating Security into the Software Development Life Cycle
Application security can be obtained and maintained only through a combination of activities — external testing of applications, application architecture reviews, source code reviews, database audits, continual training of development and security personnel, and implementation of security controls throughout the software development lifecycle (SDLC) processes.
Capstone Secure Development Services
Application Penetration Testing
The overall goal of an application penetration test is to uncover software vulnerabilities, demonstrate the impact of weaknesses, and provide recommendations for mitigation. Our team provides a detailed and in-depth security analysis of your organization’s critical applications.
Threat Modeling
Capstone’s threat modeling service helps identify over 75 percent of major security design flaws, reduces the scope of security code reviews to only those lines and components that matter, narrows and guides the focus of penetration tests, and minimizes the need for expensive code rewrites when problems are discovered.
Code Reviews
Security code reviews help software development teams find security bugs early in the development cycle. In 2011, Forrester reported that it can cost up to 30-times more to fix security bugs later in the development process. Not 30 percent more, but actually 30-times more!
Secure Policy Creation
Studies have consistently shown that building security in early, and throughout the software development lifecycle, is the most effective approach in achieving assurance. With that in mind, Capstone creates a comprehensive set of policies, guidelines, and standards that provide development teams with the resources and knowledge necessary for building reliable, rugged, and secure software.